Database Passthrough Authentication
This feature is currently in open beta for Databricks with support for additional databases coming soon. Please contact us to get access to the beta program.
Introduction
Database passthrough authentication allows organizations to enforce data security policies at the data warehouse level rather than within individual applications. This approach provides several key benefits:
- Centralized Security Management: Apply the same data security policies across multiple applications and tools
- Granular Access Control: Leverage your existing role-based access controls (RBAC) from your data warehouse
- Reduced Duplication: Eliminate the need to maintain separate security configurations in each BI tool
- Consistent User Experience: Users access data with the same permissions they have in the data warehouse
With Holistics' passthrough authentication feature, users authenticate using their individual database credentials stored as user attributes. Holistics then uses these credentials to connect to the database, ensuring that data access respects your warehouse's security policies.
Step-by-Step Setup
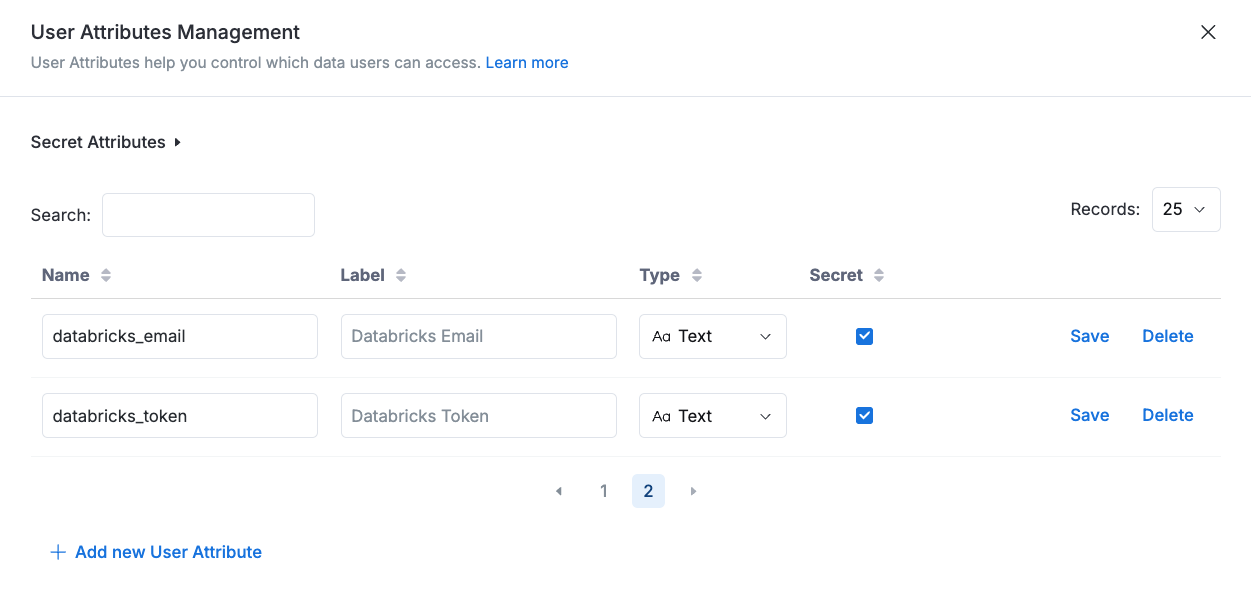
Step 1: Configure User Attributes for Credential Storage
-
Create Secret User Attributes:
- Navigate to: Organization Settings > Users > Click on "Attributes" for any user
- Create new attributes with the "secret" type enabled
- Secret attributes are exclusively used for passthrough authentication and are completely hidden from users throughout the application
-
Assign Attribute Values:
- Fill the credential values for each user through the user management interface
- Values can be managed individually or bulk-updated via API
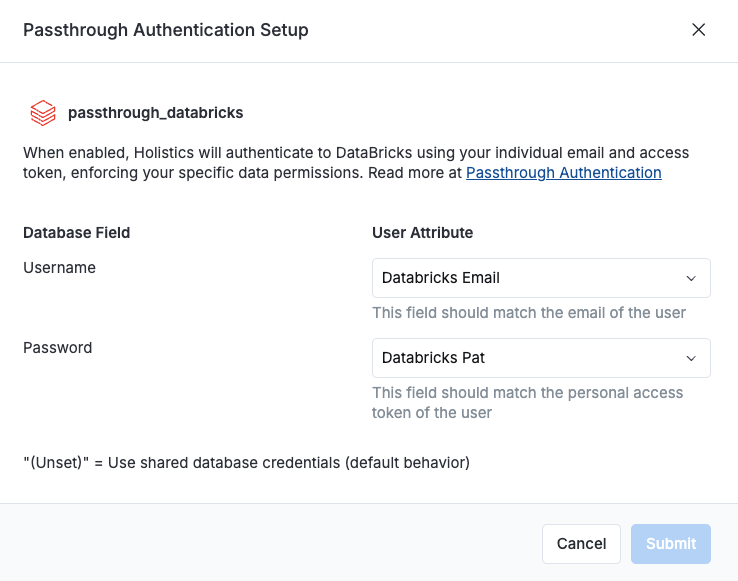
Step 2: Configure Data Source for Passthrough Authentication
- Navigate to: Data Sources
- (Recommended) Create a new data source for testing passthrough authentication
- Click the "Passthrough" in the listing of data sources
- For each configurable database parameter, select the corresponding user attribute from the dropdown
Impacted Features
Once setup, all features will leverage the database credentials to authenticate with the database, such as:
- View a dashboard
- Explore data on a dashboard
- Explore data on a dataset/data model
- Run a SQL in the query editor
- View suggestion values of a filter
- Email/Slack/Google Sheet/Data Alert/Webhook
- Direct Data Export: Excel, CSV
- and more...
These features will not work with passthrough authentication:
Frequently Asked Questions
Q: How does passthrough authentication affect data caching?
A: Each user will have their own private cache to ensure data security.
Q: Can I use both shared and personal authentication simultaneously?
A: No, Holistics will only use the personal credentials, this is to ensure that the data access is consistent and secure.
Q: How are credentials secured within Holistics?
A: Credentials are stored as secret user attributes, which are:
- Fully encrypted
- Completely hidden from users throughout the application (except for admins)
Q: Can I automate credential management?
A: Yes, Holistics provides comprehensive APIs for programmatic credential management via User Attributes API.